10 things a scaleup business could do right now to improve business security
Almost half of businesses (46%) and a quarter of charities (26%) report having cyber security breaches or attacks in the last 12 months, and the average cost to a small business when this happens is £3,230 in direct costs for each occurrence.
With an increase in home working, we assume that the most common breaches will be more effective as we communicate as teams more remotely and asynchronously.
Common Attacks
According to the Cyber Security Breaches Survey 2020, these are the most common attacks
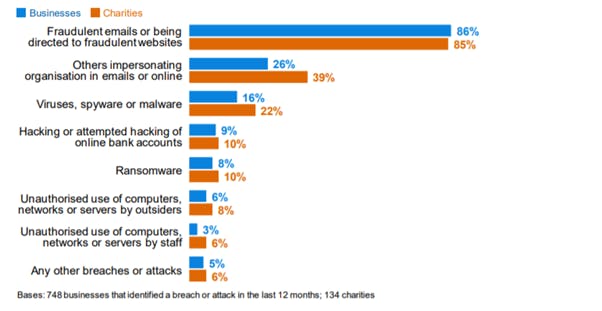
Credit: gov.uk
- 86%: Fraudulent emails or being directed to fraudulent websites
- 26%: Others impersonating organisation in emails or online
- 16%: Viruses, spyware or malware
- 9%: Hacking or attempted hacking of online bank accounts
- 8%: Ransomware
- 6%: Unauthorised use of computers, networks or servers by outsiders
- 3%: Unauthorised use of computers, networks or servers by staff
Below are a set of easy steps you could take to better protect yourself, and your business, or highlight areas of risk to mitigate with further information.
1. Add external email warning banners
It’s fairly simple for a malicious actor to send you an email pretending to be one of your colleagues. An example of this is a CFO or financial controller getting an email from the ‘CEO’ asking for urgent payment of an invoice, or other valuable information.
A quick way to make this scam obvious is to automatically add a warning to all incoming emails which are not from within the organisation.
A banner like this is hard to miss, and a clear warning to be careful. Backing this with the education of staff members on how to spot phishing attempts, will help you mitigate 86% of reported attacks. NCSC have a great article on spotting and mitigating these attempts, this should be circulated to staff.
Recommendations:
Set up an external recipient/sender warning
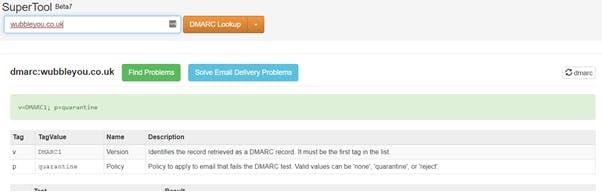
2. Check email security and anti-spoofing is configured correctly
You may check this yourself here, all you need to do is add your website address (from which your emails are sent), and submit it. If you get a red banner back, speak with your IT/email provider about correctly configuring SPF, DKIM and DMARC, more info here.
Good
Bad
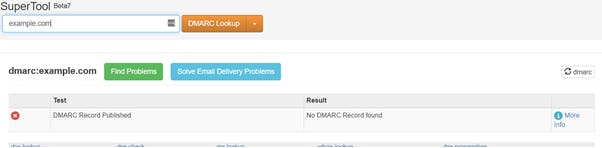
If you have a Gmail account, you may also send that an email from the email account you want to test, and follow the instructions below to ensure your anti spoof protection (SPF, DKIM and DMARC) are set correctly.

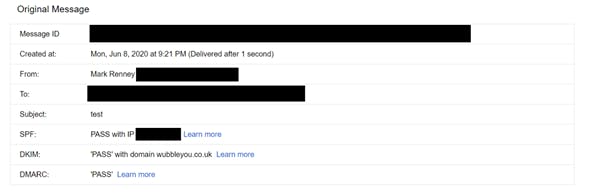
Recommendation:
- Check that this is configured correctly, and if you get an error back, speak with your IT provider and ask them to rectify it
3. Use Stack or Teams for internal communication, rather than email

Credit: Slack
If email is not used for internal communication, it can be ruled out completely as an attack vector.
Slack and Teams provide hubs for real time internal communication, leaving email just for interfacing with the outside world.
Recommendation:
- Consider using a different tool than email for communicating internally for day to day acitivities, reserving email for speaking with the rest fothe world
4. Make sure you are alerted if you, or your staff, have an account which is compromised in a data breach
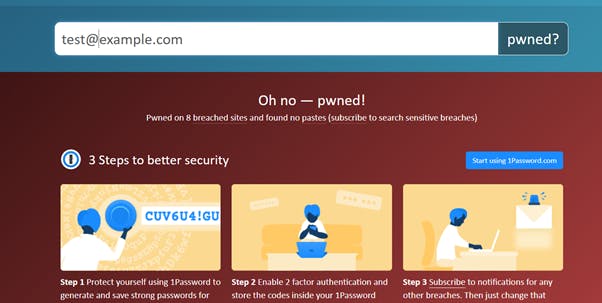
Credit: HaveIBeenPwned
Chances are you and all your staff members have had account details compromised. If you have a LinkedIn, Dropbox or Adobe account it’s almost certain.
HaveIBeenPwned is a free service which allows you to monitor your personal and work emails, and gives you a detailed summary of which services have leaked account details linked to you.
You may also use this to configure notifications for your personal/work email addresses, or to automatically alert you if any of your staff have been compromised. This ensures they are able to change their compromised passwords quickly to minimise impact.
Recommendations:
- Set up monitoring for your own personal email addresses
- Use the Domain Search feature to receive notifications if any of your staff member email addresses are compromised
5. Use a password manager to securely store and share passwords, and sensitive information
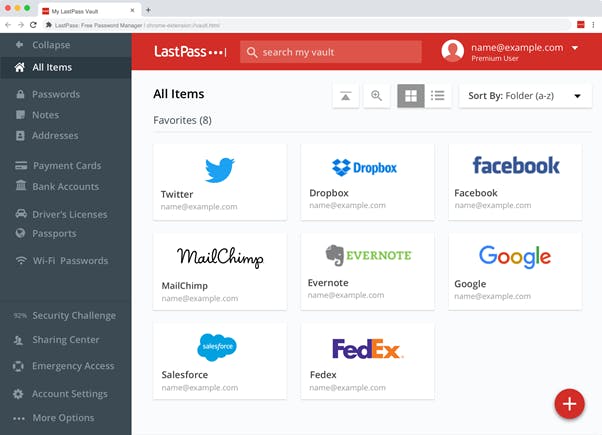
Credit: LastPass
Password reuse across services, and using weak/guessable passwords, are a major reason why accounts are compromised. If HaveIBeenPwned has flagged a compromised account, and you’ve used the same password for that as other accounts in other services, you’re at high risk of compromise there too.
All a malicious actor has to do is copy your known email/password combination from the breached service, and try in on other services, like LinkedIn, your bank account or your email account. This is called Credential Stuffing, and it’s dangerous because it’s easy.
The easiest way to prevent this, is to use a unique password for every service you use. The best way to manage that is with a password manager. Then, you only need to remember one strong password (for your password manager), and the password manager will automatically create and save very strong passwords for all your other accounts.
If you’re not using one already, set a target to start using one. As a brucey bonus, you’ll be able to share passwords amongst your team securely, no more sticky notes or emailing passwords.
Recommendation:
Use one of the following services:
- https://www.lastpass.com/
- https://1password.com/
- https://www.dashlane.com/
- https://www.okta.com/topic/password-management/
6. Enable Multi Factor Authentication (MFA) for everything
MFA means that to log into a service, you need a password, and something else to prove you are you. This is normally a phone app, physical device, or a code SMSed to you.
MFA is a second line of defence, an attacker must compromise your password and a physical device to break into your account, which would be highly targeted and difficult. This looks like:
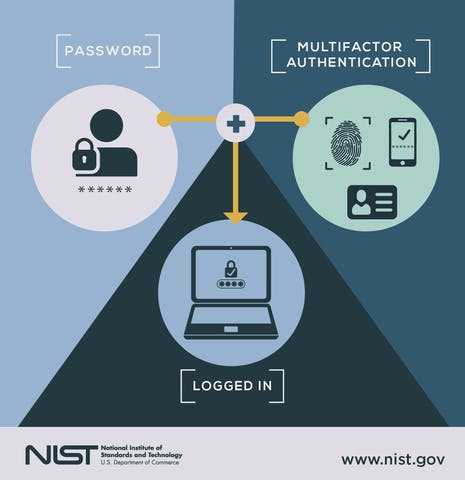
Credit: NIST
Nearly every major service has this option, and this should be enabled ASAP. It will most likely be in your account settings, there is a LinkedIn example below:
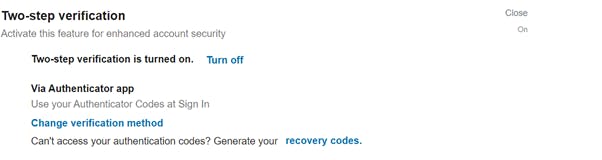
You can pair this with a phone app like Authy to automatically generate codes for your accounts, these change every 30 seconds:
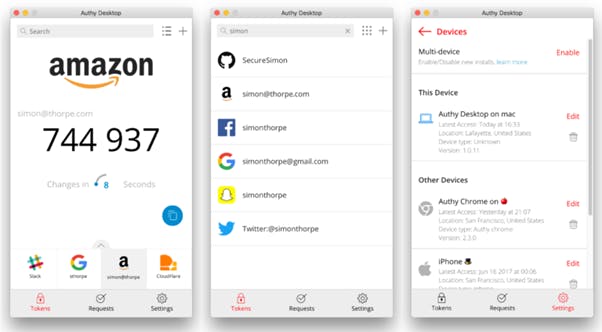
Credit: Authy
When you pair this option with a physical YubiKey (which you plug in and press), you’ve got a really solid process for securing all of your accounts in a convenient way, especially combined with a password manager.

Credit: Yubikey
Recommendations:
- Protect all services with MFA
undefinedundefinedundefined - Use Authy (or a similar app) to generate MFA codes
- Use YubiKey as a physical alternative to Authy (great if you lose access to your phone), and usually quicker than Authy
- Make it policy that all staff must do this for every service, naming business critical accounts which must be protected
You may read more on MFA at NIST here.
7. Enable device encryption for all devices

If a laptop was lost or stolen, what data/access/credentials would be on it which would cause you sleepless nights?
Mitigate that risk by encrypting anything which leaves the office, and preferably everything which stays there too.
Recommendation:
Microsoft, Android and Apple have made it super easy to encrypt devices, you may follow the guides below to achieve that:
8. Ensure all key files are backed up regularly and stored safely
Credit: Dropbox
Ransomware is an attack whereby the malicious actor encrypts all your data on your computer, and then blackmails you, usually restoring the data when you pay up.
The internet is rife with horror stories, such as ‘Hackers steal data for 15 million patients, then sell it back to lab that lost it’ - imagine explaining that to your customers!
If you have a shared network drive with no backup capability, and then one user with access is compromised, you are all toast.
A quick way to resolve this may be to migrate your shared file system over to a cloud storage provider such as Dropbox, One Drive or Google Drive.
Dropbox business provides 180 days version history, and the rewind feature allows you to revert whole files and folders to a previous point in time, so reversing the damage of a ransomware attack may be a trivial activity, if configured correctly.
It should be noted that a cloud storage system in itself is not a backup solution, but if you have nothing now, this will be better than that. It will depend on your tolerance for risk, but if the data is business critical, consider backing that up into Amazon S3 or Backblaze.
Recommendation:
If you have no backup solution in place, start with a cloud storage provider for a quick solution, and seek advice from a professional IT company.
9. Avoid public Wi-Fi, or Wi-Fi networks you do not trust

Credit: NCSC
Open Wi-Fi networks create an easy opportunity for other parties to snoop. Under the right conditions, it is possible for another user to see everything you do. Sitting on airport or café Wi-Fi creates risk.
Recommendations:
- Only connect to networks you trust, and never a Wi-Fi network which requires no password
- If you must connect to unsecured Wi-Fi, use a VPN which you trust
- Prefer tethering your phone, and connecting to the internet via 4G
10. Ban all removeable storage devices

USB storage creates 2 key risks:
- Transmission method for viruses
- A loss of control of the data which is stored on them, who knows where it will end up. Edward Snowden famously ransacked the NSA with a USB thumb drive.
In today’s world, it’s easy to securely share data using cloud storage services, and they generally provide logs for auditing purposes. You could still encrypt this data before sharing when using cloud storage, to offer similar privacy as an encrypted USB.
Recommendation:
- Ban the use of removable media throughout the business
Other Considerations
This article only tackles the easy wins, there will be value in also considering the following:
- Ensuring all devices have firewalls and Anti-Virus enabled
- Ensure all key services are protected by a Virtual Private Network or Zero Trust security
- Ensure only trusted devices are used in your business. Staff working from home using personal devices creates risk, they are not likely as secure
- Establish what your ‘Crown Jewels’ are, what data/service MUST you protect at all cost, and what do you need to do to protect that?
- If you have any internally created software, pen test this on a schedule
Will Working from Home change things?
It’s a sensible assumption that the answer is ‘Yes’. There are several avenues to consider:
Changes in climate create tension, and tension creates exploitable opportunities
NCSC has flagged an increase is COVID-19 related scams and phishing emails, scaring recipients to open malicious URLs and file attachments.
Working from Home may be new territory for some, security has been weakened
Businesses new to this way of working, may not have mature policy and process for securely allowing staff to conduct their day to day activities from home. It’s a reasonable assumption that some businesses may have weakened their security to allow for this, such as bypassing VPNs or allowing use of personal devices. Businesses which have not before needed to securely share data in a remote way, may now need to.
Risk in these areas must be considered, and mitigated, or businesses create avenues for exploitation.
We are communicating less in person, and more asynchronously and online
This creates opportunity for malicious actors to impersonate people of authority and socially engineer others into doing things they should not. A common scam right now is to trick staff into paying rogue invoices or handing over data, this may trend up.
Conclusion
Cyber security is hard. To be compromised, you only must get one thing wrong, and an attacker, one thing right.
However, with some quick and simple steps, you’re able to help mitigate a lot of risk.
In summary:
- Reduce impact of phishing/spear phishing attacks
undefinedundefinedundefined - Reduce impact of account hijacking/unauthorised access
undefinedundefinedundefined - Reduce chance of unauthorised use/access of devices
undefinedundefinedundefinedundefined - Reduce impact of ransomware
undefinedundefined
What next?
Has Cyber Security become more of a focus in your organisation?
Feel free to reach out to us to send us your thoughts!

